The Internet of Things (IoT) is a network of devices, vehicles, home appliances, and other items that use sensors, software, and network connectivity to collect and exchange data. These devices are changing the way we live, work, and communicate. However, they are also opening new avenues for crime. In fact, IoT devices are among the most vulnerable equipment in the world.
Massive cyber-attacks are on the rise. According to the latest statistics, global IoT cyberattacks increased by 38% in 2022, compared to 2021. 83% of organizations working with the IoT technology had more than one data breach in 2022, while 82% of all breaches involved 'the human element' (the use of stolen credentials, phishing, or human error).
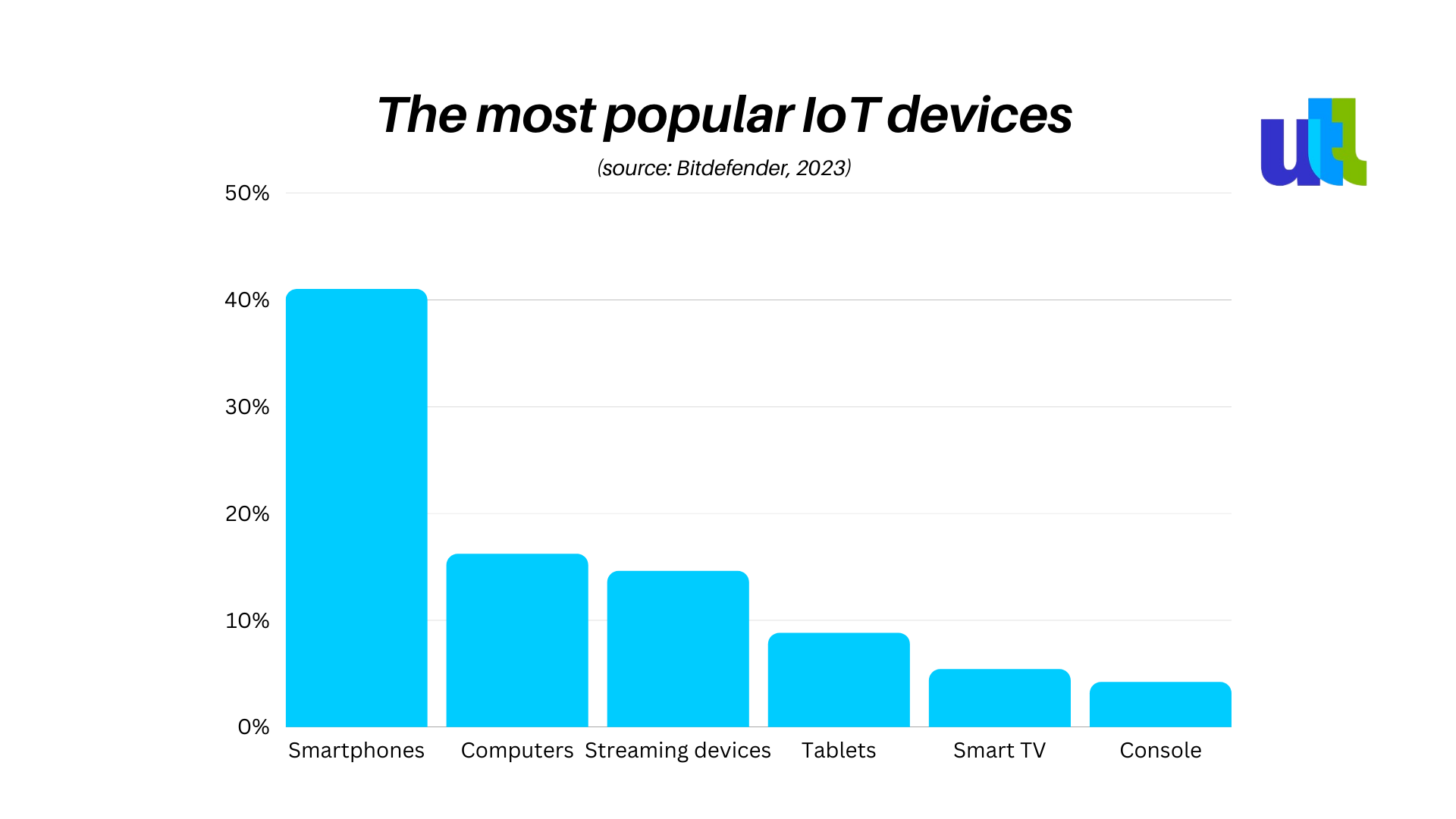
And although this type of attack targeting data have gotten the most attention in recent years, threats that can take out infrastructure, including IoT hardware, also bring a significant risk for organizations deploying connected devices.
For example, IoT hardware is often more physically accessible than traditional pieces of computer equipment. That means sensors and edge devices, such as gateways, can be more easily displaced or damaged -- either accidentally or intentionally -- through physical actions. Such endpoint devices have limited computational and power resources by design. That means they often can’t support advanced security features. They generally can't - or can't easily - be updated to address vulnerabilities as in the case of software.
Understanding IoT Security
IoT Security is the act of securing connected devices and the networks they’re connected to from threats and breaches by protecting, identifying, and monitoring risks - all while helping fix vulnerabilities and minimize their number.
The practices and technologies used to secure connected devices are constantly evolving because new types of hacks and security threats are discovered all the time. That means a robust IoT security solution must include features and the latest practices that keep connected systems secure today and tomorrow.
IoT security requirements can only be met with an integrated solution that delivers visibility, segmentation, and protection throughout the entire network infrastructure.
Your solution must have the following key abilities:
Learn: with the right knowledge, you can build a risk profile and assign them to IoT device groups.
Segment: IoT devices can be segmented into policy-driven groups based on their risk profiles.
Protect: the internal network segmentation enables monitoring, inspection, and policy enforcement based on the activity at various points
Organizations often lack the required expertise, underestimate the threats, and misjudge the risk.
Risks of the IoT Ecosystems
- Customer data exposure — many IoT devices collect and transmit sensitive data that could be used maliciously.
- Corporate data exposure — the IoT devices connected to a company’s data center open security holes and may cause catastrophic vulnerability and data loss.
- Physical damage — many actuators have risks of physically harming customers (such as heating elements).
- High-risk downtime —fatal threats in the case of service failure, IoT devices may be beyond the skillset of an in-house team.
- Reputation and brand damage — corporations can suffer massive losses after a security attack because of large-scale news event that damages their reputation.
However, developers and decision-makers can combat the risks by preventing potential attacks and taking actions to ensure the continued safety of their connected systems.
Ways to protect an IoT ecosystem
These are the areas, features, and key actions to review if you want to create a secure system in a rapidly evolving IoT field.
1. Operating Systems — each open port and available protocol is a potential point of attack.
2. Applications — the more applications you have, the more potential there is for bugs or security vulnerabilities.
3. Dependencies — modern encryption and communication protocols change and evolve over time, and you should not risk ignoring new vulnerabilities. A larger number of dependencies means more maintenance actions must be planned.
4. Communication — there are dozens of potential threats that can occur if communications between the device and the cloud are not encrypted, or are encrypted poorly. Ensure the proper encryption by growing the levels of confidentiality, integrity, and authenticity.
5. Cloud — a cloud requires constant monitoring and testing. Integrating security mailing lists and alerts for your dependencies, operating systems, and service providers is the first step towards protecting the data on the cloud.
6. User Access and Security — constantly educate your team by updating them on the latest security measures and awareness, phishing and, social engineering attacks. Integrate practices like two-factor authentication, strong passwords, and whole-disk encryption to reduce the risks coming from careless user errors.

And numerous small ones.
The truth is… all systems require maintenance to stay ahead of evolving security risks.
At Utah Tech Labs, we use at least 3 features and actions that help us prevent most of future vulnerabilities:
- Penetration testing — we stay ahead of modern hacking techniques by repeatedly testing our systems with security researchers and fixing potential vulnerabilities while developing.
- Firmware application reviews — our security experts sanitize application flaws during firmware development, thus, preventing fatal application flaws at a customer level.
- Security update mechanisms — we know security protocols change and improve over time, and we never miss a thing.
Furthermore, we use hardware keys and two-step authentication, organize team access controls, conduct continuous monitoring and OTA firmware updates, encrypt every connection, and respect even the smallest data policy.
We are convinced that the best practice for securing any enterprise technology, including IoT devices, brings together multiple layers of protection -- in this case, a combination of hardware-based security, software, and legal policies.
By partnering with Utah Tech Labs, you have full access to high-level IoT experts, a large community of IoT enthusiasts, support services, and professional engineering services. Start your IoT journey today.
For free consultation on IoT security landscape click here.
----------------------------------------------------------------------------------------------
View the full presentation:
WRITTEN BY
Sofia Kutko
2023-07-04